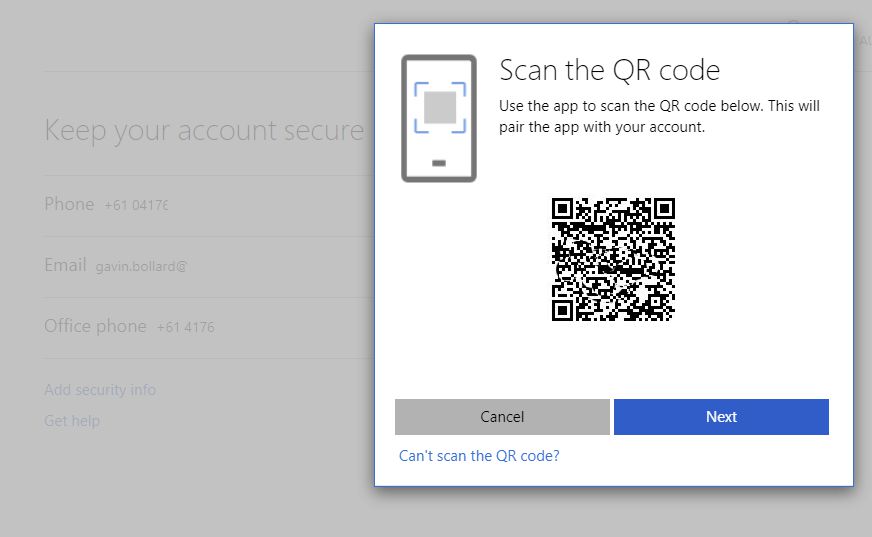
Connecting to remote resources: A crucial link for seamless access.
This URL represents a direct link to a service facilitating remote access to resources. It likely provides a gateway for users to connect to applications, files, or devices situated on a network or cloud system. This connection often involves a secure protocol, such as RDP (Remote Desktop Protocol), ensuring confidentiality and integrity of data transfer. For example, a user might employ this link to access work documents from home or to remotely control a server from a different location.
The significance of this service lies in its ability to streamline communication and collaboration regardless of geographical limitations. By enabling remote connectivity, efficiency and productivity can be enhanced. Access to shared resources improves team performance in distributed work environments, reducing the need for physical presence and enabling work from any location. The service's ease of use and security features are key to its effective deployment in various professional contexts.
Read also:Gavin Newsom Kimberly Guilfoyle Wedding Photos Exclusive Pics Details
The specifics of the linked service, including application compatibility, security protocols, and supported operating systems, should be documented for further details.
https//aka.ms/remoteconnect
This link facilitates remote access, a critical element in modern work environments. Understanding its components is essential for efficient use.
- Remote access
- Secure connection
- Resource sharing
- Network protocols
- User authentication
- Application compatibility
- Platform diversity
- Data integrity
The link's purpose hinges on remote access. Security relies on secure connections, leveraging robust protocols. Resource sharing enables collaborative work. Efficient network protocols ensure reliable transmission. User authentication verifies legitimate access, and application compatibility ensures seamless interaction. Support for diverse platforms, like Windows and macOS, broadens accessibility. Ultimately, data integrity safeguards information. For example, this link might allow a team member to access critical files from a different location while adhering to robust security measures. These factors collectively contribute to a productive and secure remote work environment.
1. Remote access
The URL "https//aka.ms/remoteconnect" is likely a gateway to remote access services. Remote access, in this context, refers to the ability to connect to and utilize resources (like files, applications, or devices) from a location other than where the resources reside. This capability is a fundamental component of the link, allowing users to interact with systems and data remotely. A critical function of this link is establishing a secure connection, enabling remote operation of computers and network devices.
The practical significance of understanding this connection is substantial. Successful remote access hinges on effective security protocols, efficient communication channels, and appropriate user authentication. For instance, a company's remote access system might allow employees to access confidential documents from home, supporting remote work initiatives and flexibility. Similarly, technicians might remotely diagnose and repair equipment, leading to quicker resolutions and minimized downtime. Proper configuration and maintenance of the remote access infrastructure, encompassing firewalls and encryption, are essential to safeguarding sensitive data and maintaining system stability. A robust security framework within the linked remote access system minimizes the risk of unauthorized access and data breaches.
In conclusion, the connection between remote access and the URL underscores the importance of secure remote operation and resource management. Understanding this link's function within a larger framework of remote access systems is essential for effectively utilizing and maintaining such infrastructure, ensuring data integrity and operational efficiency. Careful consideration of security protocols and user authentication is crucial in ensuring the safety and integrity of remote access systems.
Read also:Youll Never Believe What Tom Cruise Is Up To Now
2. Secure Connection
The secure connection element is paramount to the function of "https//aka.ms/remoteconnect." This link likely facilitates remote access, requiring a secure channel to protect data transmitted between users and resources. Compromising this security could lead to data breaches and system vulnerabilities. Establishing a secure connection is therefore essential for ensuring confidentiality, integrity, and availability of data in the context of remote interactions.
- Encryption Protocols
Secure connections rely heavily on encryption protocols like TLS (Transport Layer Security) or its predecessor, SSL (Secure Sockets Layer). These protocols encrypt data transmitted over a network, rendering it unreadable to unauthorized parties. This protection is crucial for safeguarding sensitive information exchanged through the link, especially in sensitive scenarios like financial transactions or data transfer in business environments. For example, secure remote access to a company's servers for data retrieval would employ encryption.
- Authentication Mechanisms
Ensuring only authorized users access the resources is critical. Authentication mechanisms, such as usernames and passwords or multi-factor authentication, are employed to verify user identities. This prevents unauthorized access and misuse of the connection, protecting the system's integrity and resources. Robust authentication is vital in ensuring the security of the link to prevent malicious actors from gaining access to the remote resources.
- Data Integrity Verification
Data integrity verification ensures that data transmitted remains unchanged during transmission. Mechanisms like checksums or digital signatures are used to detect any alterations, thus preventing tampering. This verification is paramount when dealing with sensitive information to prevent unauthorized modifications that compromise data accuracy and reliability.
- Network Security Measures
Firewall configurations and intrusion detection systems form the bedrock of network security. These measures prevent unauthorized access and protect the connection from malicious activities. This is vital to safeguard the integrity of the remote access service by blocking unauthorized access attempts and preventing data breaches.
In summary, the security of the connection facilitated by "https//aka.ms/remoteconnect" relies heavily on a combination of strong encryption, robust authentication, data integrity verification, and robust network security. These measures collectively ensure that only authorized users can access intended resources, maintain data accuracy, and protect the system from malicious activities.
3. Resource Sharing
The concept of resource sharing is intrinsically linked to the function of "https//aka.ms/remoteconnect." This URL likely facilitates access to shared resources across a network, enabling users to collaborate and utilize data and applications located remotely. Understanding this aspect provides insights into the service's utility and security considerations.
- File Sharing and Collaboration
The link likely facilitates sharing and accessing files stored on centralized servers. This enables teams to collaborate on documents, spreadsheets, or other files simultaneously, regardless of physical location. Such collaborative access is crucial in project management, marketing campaigns, or other team-based activities. For instance, team members might access and modify a shared project document remotely, fostering real-time interaction and efficient workflow. This element directly supports the URL's function by facilitating the sharing of project materials.
- Application Sharing
Certain services accessed via the URL may facilitate sharing applications among users. This allows users to work with specific applications from different locations without having to install them locally. For instance, access to specialized software or complex modeling tools might be remotely available via the link. Remote access to applications promotes consistency and uniform work processes for teams using distributed setups.
- Device Sharing (and Control)
The URL might potentially facilitate the sharing of network devices (servers, storage arrays) via remote management. This allows for streamlined centralized management and maintenance across locations. System administrators can remotely access and control shared network devices without physical presence, which is critical for network uptime and operational efficiency. For instance, troubleshooting network issues, deploying updates, or managing storage capacity can all be handled remotely through a service connected to this URL.
- Security Considerations for Shared Resources
Safeguarding shared resources is paramount. Access control mechanisms are necessary to ensure only authorized users can access specific resources. This aspect is tightly linked with secure connectivity elements and ensures the confidentiality and integrity of data. Implementing robust security protocols prevents unauthorized modifications or access attempts, thus maintaining the reliability and trustworthiness of the shared resources. Effective user authentication, access permissions, and encryption protocols are crucial for the secure sharing of resources in the context of remote access.
In conclusion, resource sharing via a service connected to "https//aka.ms/remoteconnect" offers several advantages in terms of enhanced collaboration, remote access, and streamlined workflows. However, the secure and responsible management of shared resources is paramount to maintain data integrity and prevent potential breaches. The security measures implemented within the shared resource system are crucial for maintaining trust and reliability.
4. Network Protocols
Network protocols are fundamental to the operation of "https//aka.ms/remoteconnect." This URL likely facilitates remote access, a service reliant on established protocols to govern communication between devices and resources. These protocols define the format, structure, and rules of data transmission, ensuring reliable and secure interactions. Without appropriate network protocols, the remote access service would be unreliable or susceptible to security breaches. Specific protocols like TCP/IP (Transmission Control Protocol/Internet Protocol) underlay the service, allowing for data transmission over a network. The use of secure protocols like HTTPS further enhances security by encrypting data exchanged, protecting sensitive information from unauthorized interception. These protocols, combined with security measures, determine the reliability and security of the remote connection.
Understanding the specific network protocols employed by the linked service is vital. For example, knowledge of the protocols used for authentication (e.g., Kerberos, LDAP) reveals the security mechanisms in place. The protocols utilized for file transfer (e.g., SMB, FTP) define how shared data is exchanged. Analyzing these protocols provides insights into the limitations and security features of the remote access service. This comprehension is crucial for system administrators configuring and maintaining secure remote connections, as well as users interacting with the service. A detailed knowledge of the protocols used allows for effective troubleshooting of network issues and ensures proper functioning of the service.
In summary, network protocols are integral to the functionality and security of "https//aka.ms/remoteconnect." The selection and implementation of appropriate protocols directly impact the reliability, security, and efficiency of the remote access service. Understanding these protocols allows for a more nuanced perspective on the workings of remote access systems, enhancing overall system administration, security, and user experience. A thorough understanding of the specific protocols in use allows for a comprehensive assessment of the service's security and for potential vulnerabilities to be recognized and mitigated.
5. User authentication
User authentication is a critical component of "https//aka.ms/remoteconnect." This URL likely represents a service requiring verification of users' identities before granting access to resources. Robust authentication mechanisms are essential to prevent unauthorized access and maintain the integrity and security of the linked service. Failure to properly implement and maintain authentication can lead to significant vulnerabilities. The security of sensitive data and system resources hinges directly on effective authentication procedures.
The importance of user authentication within the context of remote access is magnified by the inherent risks associated with distributed systems. Unauthorized individuals gaining access to resources through compromised credentials can cause significant harm. Examples include data breaches, manipulation of sensitive information, and disruption of operations. Effective authentication measures, such as strong passwords, multi-factor authentication (MFA), and access controls, mitigate these risks. A service like "https//aka.ms/remoteconnect" would likely employ a combination of methods to verify user identity, incorporating factors such as knowledge (passwords), possession (tokens), and inherence (biometrics). The authentication process safeguards against unauthorized access by ensuring only legitimate users can interact with the service and its resources.
Understanding the connection between user authentication and a service like "https//aka.ms/remoteconnect" is crucial for both administrators and users. Administrators must implement and maintain robust authentication systems to protect the service from vulnerabilities. Users should be aware of best practices, such as strong password creation, and avoid potential security pitfalls. Effective authentication is not just a technical requirement; it's a vital security measure ensuring the integrity of the service and safeguarding sensitive data in distributed environments. A breakdown in authentication can severely compromise the entire system. Proper user training and implementation of strong authentication methods are fundamental for preventing potential security breaches and preserving trust in the remote access service. The practical significance of understanding this principle lies in proactively mitigating potential threats and ensuring a safe and reliable online experience.
6. Application Compatibility
Application compatibility is a critical factor when considering a service like "https//aka.ms/remoteconnect." This link likely provides remote access to resources, and the successful operation of these remote connections hinges on the compatibility of applications with the remote environment. Compatibility issues can manifest as application malfunctions, data corruption, or, in severe cases, system instability. Applications reliant on specific hardware configurations or operating systems may not function correctly if the remote environment lacks the necessary components. Consequently, the compatibility of applications with the remote environment influences the usability and reliability of the service itself.
Real-world examples illustrate the significance of application compatibility. Imagine an employee needing to access a specialized software package from a remote location. If the application isn't compatible with the remote server's operating system or lacks the required drivers, the software may not function correctly, impacting productivity. Similarly, a complex financial application might struggle to connect to a remote database if the required network protocols or security measures are not compatible. These scenarios underscore the need for meticulous compatibility testing and configuration to ensure smooth operations in remote environments. Applications needing specific security protocols or particular types of network connectivity should be considered carefully to avoid compatibility issues.
Understanding application compatibility within the context of "https//aka.ms/remoteconnect" is essential for both administrators and users. Administrators must ensure the compatibility of applications and services accessible through the link. Users need to understand the technical requirements of the remote applications they intend to use. The knowledge of application compatibility allows for effective troubleshooting and maintenance, preventing unexpected operational failures. A robust understanding also empowers users to anticipate and address compatibility issues in advance, preventing difficulties and optimizing the usage of the remote access service. Ultimately, this understanding ensures seamless and reliable access to remote applications, directly impacting user experience and system efficiency.
7. Platform Diversity
The capability of "https//aka.ms/remoteconnect" hinges on its ability to function across diverse platforms. This broad compatibility is crucial for accessibility and utility. A service facilitating remote connections must accommodate various operating systems (e.g., Windows, macOS, Linux) and devices (desktops, laptops, mobile phones) to reach a wider user base. Limitations in platform diversity restrict the service's usefulness and potentially exclude significant portions of the user population. For instance, a remote access system designed solely for Windows users would severely limit its applicability.
The importance of platform diversity is multifaceted. A service capable of connecting across platforms ensures greater flexibility and accessibility. Employees can access crucial data and applications regardless of the device they use. Students can access educational resources from diverse devices. Healthcare professionals can remotely access patient data from various types of terminals. This adaptability is a crucial component for scalability and market penetration. Modern businesses and organizations increasingly rely on distributed workforces, and platform diversity is essential for seamless integration and efficiency. Conversely, a lack of platform diversity can lead to user frustration, decreased productivity, and ultimately, hinder the service's overall effectiveness. A service with limited platform compatibility might struggle to attract a global customer base or compete with more versatile alternatives.
In conclusion, platform diversity is a critical factor in the success of remote access services like the one potentially linked to "https//aka.ms/remoteconnect." Its ability to operate across various platforms enhances accessibility, flexibility, and market reach. Understanding this connection is essential for assessing a remote service's practical value and predicting its potential impact on diverse user groups. This understanding allows for a more comprehensive evaluation of the service, considering both technical capabilities and broader societal implications.
8. Data Integrity
Data integrity, the accuracy and consistency of data over its lifecycle, is paramount to any system facilitating remote access, such as the one potentially linked to "https//aka.ms/remoteconnect." Maintaining data integrity in a remote environment necessitates robust protocols and mechanisms to prevent corruption, unauthorized modification, or loss. The integrity of data is crucial for the reliability and trustworthiness of the system.
- Data Validation and Verification
Mechanisms for validating and verifying data are essential. This includes checks to ensure data conforms to expected formats and ranges. For example, validating input fields to prevent incorrect data entry, or employing checksums to detect changes during transmission, ensures data integrity. Errors in remote data entry or during file transfer can severely compromise data accuracy and necessitate corrective actions. Proper validation prevents erroneous data from entering the system and subsequently distorting downstream processes.
- Data Encryption and Secure Transmission
Protecting data during transmission is paramount. Employing encryption protocols ensures that data remains confidential and unaltered while in transit. For example, encrypting sensitive data exchanged over the network or using secure channels for file transfer prevents unauthorized access or modification. The security protocols employed directly impact data integrity by preventing tampering and unauthorized access.
- Access Control and Authorization
Restricting access to authorized personnel is crucial for data integrity. Implementing robust access controls dictates which users can access specific data and what operations they are permitted to perform. This prevents unauthorized modification or deletion of sensitive data. For instance, user roles with varying levels of access are often implemented to maintain data integrity. These restrictions ensure that only authorized individuals can modify or access data, which safeguards its accuracy and validity.
- Backup and Recovery Procedures
Maintaining regular backups and establishing effective recovery procedures are vital. Data loss can occur due to system failures or malicious activity. Establishing robust backup and recovery protocols allows for the restoration of data in case of a disaster or corruption. In a remote access environment, these procedures are doubly important to ensure business continuity and minimize data loss. Backup strategies need to be tailored to the specific data needs and potential threats in the remote access system.
In summary, data integrity in the context of "https//aka.ms/remoteconnect" necessitates a multi-faceted approach. Comprehensive data validation, secure transmission, controlled access, and dependable recovery procedures are all crucial elements. Prioritizing these safeguards ensures the system maintains the reliability and trustworthiness necessary for users and organizations relying on the service, ultimately preventing data corruption and maintaining operational efficiency.
Frequently Asked Questions about https
This section addresses common inquiries regarding the remote connection service accessible via the provided URL. Accurate and comprehensive information is presented to clarify potential ambiguities and concerns.
Question 1: What is the purpose of this remote connection service?
The service facilitates remote access to resources hosted on a network or cloud platform. This encompasses accessing files, applications, or devices from a location outside the physical network. Remote connectivity enables distributed collaboration and work from various locations, while maintaining a secure connection.
Question 2: What security measures are in place?
Robust security measures, including encryption protocols, are implemented to protect data transmitted. Authentication mechanisms verify user identities, preventing unauthorized access. Access controls limit specific users' permissions to sensitive data and resources. Data integrity measures ensure data remains accurate and consistent throughout the connection process.
Question 3: What platforms are supported?
Compatibility with diverse platforms is crucial. The service ideally supports a range of operating systems and devices, ensuring broad accessibility for various user needs and configurations. Details on supported platforms should be readily available.
Question 4: How do I access the service?
Instructions for accessing the service should be readily available. This may include specific steps for initiating a remote connection, logging in, and navigating the platform. Clearly outlined procedures contribute to user proficiency and minimize difficulties.
Question 5: Are there any limitations or restrictions?
Specific limitations or restrictions regarding data transfer rates, bandwidth usage, or the types of resources accessible are critical to consider. Clear documentation outlining any constraints on use will ensure realistic expectations and appropriate resource allocation.
In summary, the remote connection service aims to provide secure, reliable, and versatile remote access. Thorough understanding of the service's features and limitations ensures efficient and secure utilization.
Further details regarding specific functionality and configurations can be found in the service documentation.
Conclusion
The URL "https://aka.ms/remoteconnect" represents a gateway to remote access services. Key aspects explored include the necessity of secure connections, effective resource sharing, adherence to established network protocols, robust user authentication, compatibility across diverse platforms, and the paramount importance of data integrity. These elements are fundamental for the reliable and secure operation of remote access systems. The exploration reveals a complex interplay of technical and security considerations in enabling remote work and collaboration. The significance of secure protocols, robust authentication, and platform compatibility are underscored to mitigate potential vulnerabilities and ensure successful remote interactions.
The implications of remote access systems, exemplified by services accessed via this URL, extend beyond immediate application. The future of work, collaboration, and access to information is fundamentally intertwined with the secure and reliable functioning of such systems. Ensuring data integrity, adhering to established security protocols, and maintaining compatibility across diverse platforms become crucial imperatives for organizations leveraging remote access technologies. A thorough understanding of these aspects is critical for navigating the evolving landscape of remote work and maintaining data security.